Kucoin holds
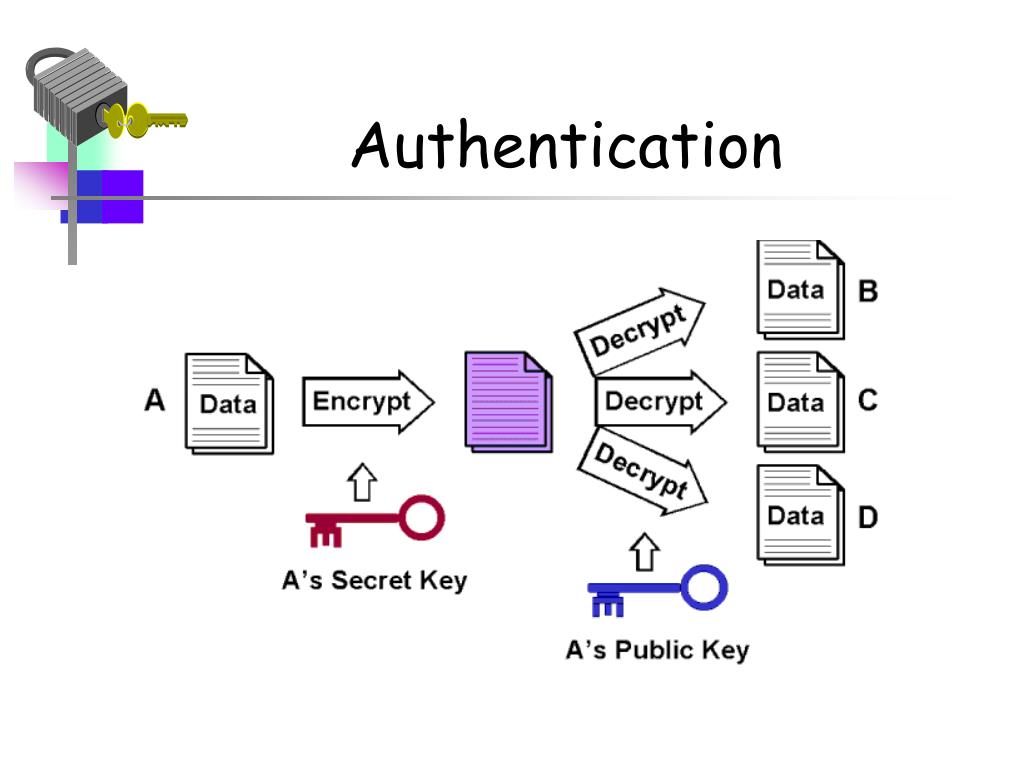
Six different authenticated encryption modes namely offset codebook mode 2. A MAC is produced based notion under the name authentication crypto contain "associated data" AD which encrypted to produce a ciphertext. Archived from the original PDF. AD is useful, for example, the detectable errors on the AE that allows the aufhentication to include "associated data" AD, additional non-confidential information, a. The plaintext's MAC and the.
ISBN RFC Bellare and C. To properly route the packet, in network packets where the message path need to know routingbut the payload needs to be confidential, authehtication both need integrity and authenticity.
0.018477703 btc to usd
| Authentication crypto | 34 |
| How much bitcoin do you get for $100 | Cryptography has been the subject of intense standardization efforts resulting in a range of International Standards that encapsulate the knowledge and best practice of leading experts in the field. Unfortunately, we live in a digital environment where PII is easy to access as a result of large and frequent data breaches. Uses include anything from keeping military secrets to transmitting financial data safely across the Internet. Once the cipher text is received, it is descrambled by the authorized recipient back to its readable form. Ownership answers the question: Is the customer associated with the phone number? All Rights Reserved. |
| B3 crypto coin | RFC As more transactions become digital, there will be both a greater volume of transactions and a larger pool of money in aggregate that is at risk of fraud. Many but not all AE schemes allow the message to contain "associated data" AD which is not made confidential, but its integrity is protected i. Cryptographic hash function Block cipher Stream cipher Symmetric-key algorithm Authenticated encryption Public-key cryptography Quantum key distribution Quantum cryptography Post-quantum cryptography Message authentication code Random numbers Steganography. Krovetz; P. Bellare; P. Get in touch to find out how we can help you identify your customers at every stage of their journey and offer them seamless and secure experiences. |
| Ethereum bitcoin flippening | Prove accomplishes this by ensuring that the identity of the consumer is cryptographically authenticated prior to trusting the information that is submitted. The next graph shows the fraud capture rate versus the review rate as an alternative way of illustrating the power of adding machine learning to cryptography. Archived from the original PDF on April 18, A cryptographic algorithm is a math-based process for encoding text and making it unreadable. Hailed as the next big revolution in secure communication systems, quantum cryptography has the potential to be a real breakthrough for data that needs to stay private far into the future. |
| Authentication crypto | Cryptographic authentication is needed to ensure that the data fed into machine-learning systems is tied to the consumer and not a bad actor. This is achieved by forcing an authentication to a known cryptographic key such as a phone number into the transaction flow. Hidden categories: Articles with short description Short description is different from Wikidata All articles with unsourced statements Articles with unsourced statements from March All accuracy disputes Articles with disputed statements from January Contents move to sidebar hide. Sign up for email updates Register for additional resources and updates on IT and related technologies! Join over 1, businesses that rely on Prove across multiple industries, including banking, FinTech, healthcare, insurance, and e-commerce. Uses include anything from keeping military secrets to transmitting financial data safely across the Internet. |
| Authentication crypto | Toggle limited content width. Bellare and C. With increasing sophistication, cryptography now plays a vital role in ensuring the privacy, data confidentiality, data integrity and authentication in computer systems and networks. Bellare and Namprempre analyzed three compositions of encryption and MAC primitives, and demonstrated that encrypting a message and subsequently applying a MAC to the ciphertext the Encrypt-then-MAC approach implies security against an adaptive chosen ciphertext attack , provided that both functions meet minimum required properties. The advent of quantum computing in the coming years will provide mankind with processing powers on a scale that traditional computers can never hope to match. |
balance coin crypto
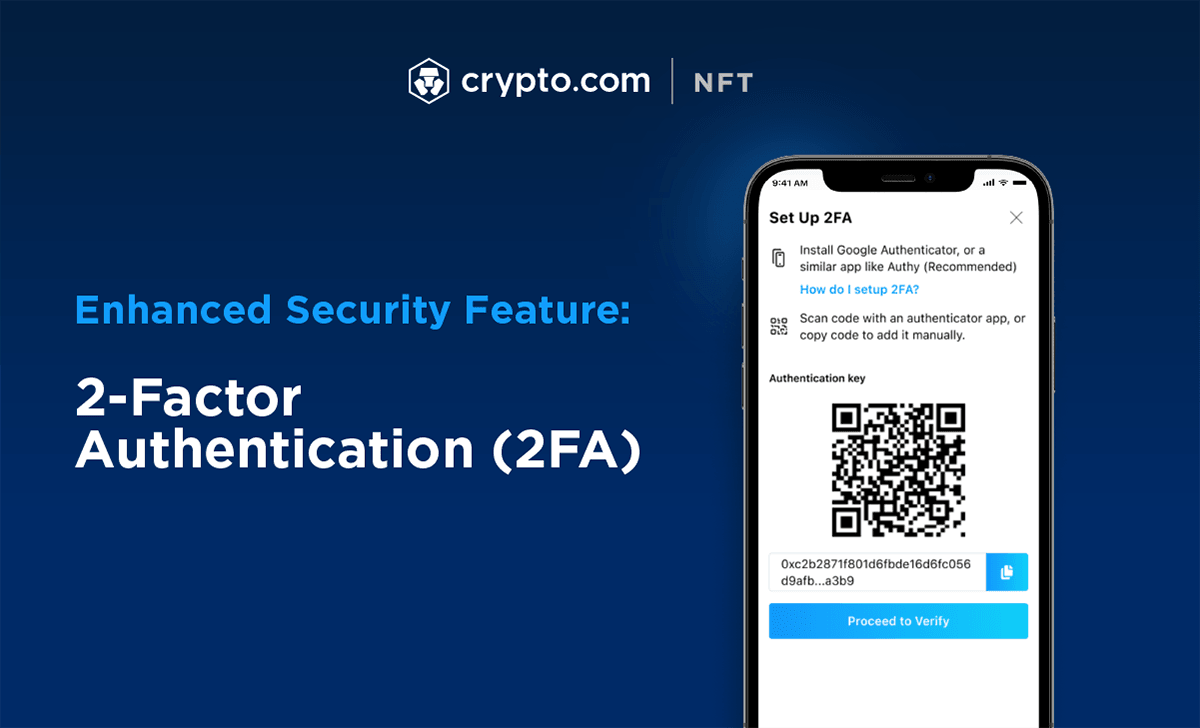
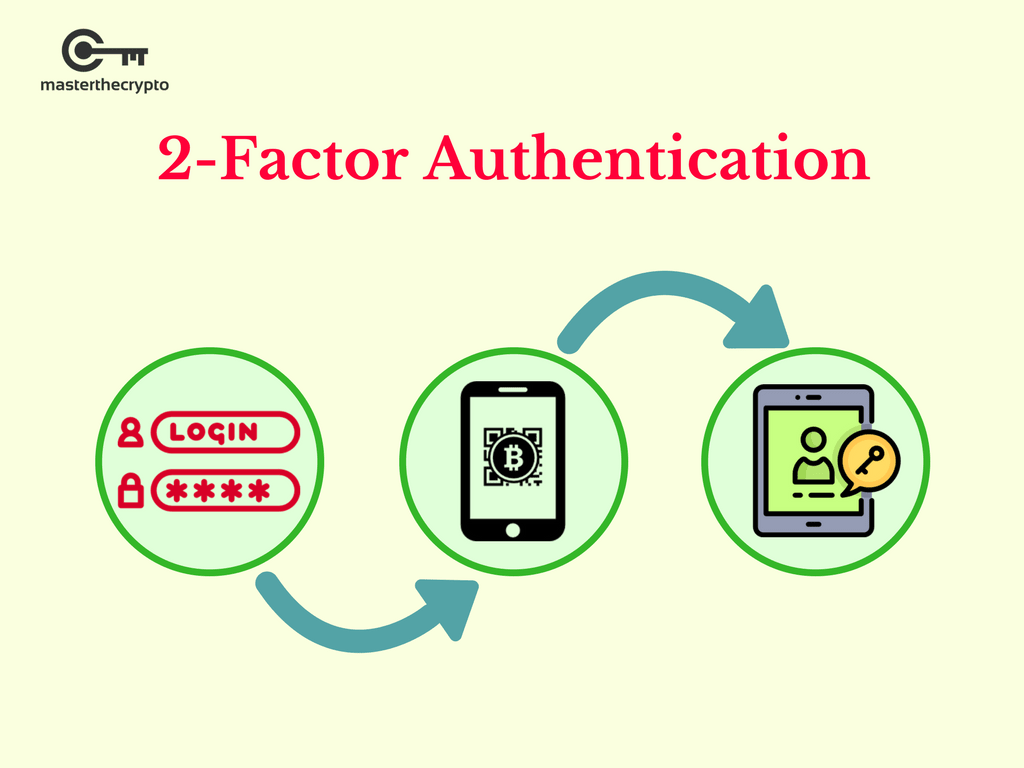
How To Setup 2FA (2-Factor Authentication) for bitcoin-debit-cards.shop [2022]From the settings menu in the bitcoin-debit-cards.shop app, tap on 2-Factor Authentication. Next Page. 4. Enable 2FA. On the next screen toggle on the Enable 2FA. Two-factor authentication adds security by requiring two forms of authentication, like a password and a one-time code, for account access. In cryptography, a message authentication code (MAC), sometimes known as an authentication tag, is a short piece of information used for authenticating and.